The focus of the security rule is to the confidentiality, integrity, and availability of electronic protected health information (ePHI) that the Yale University covered components creates, accesses, transmits or receives.
ePHI is any Protected Health Information (PHI) which is stored, accessed, transmitted or received electronically. Hence, the “e” at the beginning of ePHI.
Confidentiality is the assurance that ePHI data is shared only among authorized persons or organizations.
Integrity is the assurance that ePHI data is not changed unless an alteration is known, required, documented, validated and authoritatively approved. Most important to HIPAA, data integrity ensures that we can rely on data in making medical decisions. It is an assurance that the information is authentic and complete, and that the information can be relied upon to be sufficiently accurate for its purpose.
Availability is the assurance that systems responsible for delivering, storing and processing critical ePHI data are accessible when needed, by those who need them under both routine and emergency circumstances.
Privacy vs. Security
HIPAA regulations cover both security and privacy. While related, security and privacy are distinct.
- The Privacy rule focuses on the right of an individual to control the use of his or her personal information. Protected health information (PHI) should not be divulged or used by others against their wishes. The Privacy rule covers the confidentiality of PHI in all formats including electronic, paper and oral. Confidentiality is an assurance that the information will be safeguarded from unauthorized disclosure. The physical security of PHI in all formats is an element of the Privacy rule. See Policy & Guidelines for Physical Security.
- The Security rule focuses on administrative, technical and physical safeguards specifically as they relate to electronic PHI (ePHI). Protection of ePHI data from unauthorized external or internal access and extends to ePHI data that is stored or in transit.
Below you will find information on protecting patient privacy and security. Remember, if you have any privacy or security concerns, report them using the links on this page.
We all play a role in protecting Yale’s ongoing pursuit of excellence!
As a trusted member of Yale’s HIPAA covered entity, you have an obligation to protect patient privacy and security. This obligation begins the first day you start at Yale and continues even after you leave Yale. You must continue to protect patient information you learned of while working at Yale.
Protect HIPAA Data at Yale University
1. Ensure all devices and applications you use to access ePHI meet Yale’s Minimum Security Standards (MSS) for High Risk, HIPAA data.
- Protected Health Information (PHI) is considered High Risk data, per Yale’s Data Classification policy.
- ePHI stands for Electronic Health Information. ePHI includes any medium used to store, access, transmit or receive PHI electronically.
- This means that all devices, applications, and software used to access Yale ePHI must meet Yale’s Minimum Security Standards (MSS) for High Risk, HIPAA data.
- Examples of devices include laptop and desktop computers, smartphones, and tablets.
- Examples of applications and software include email and cloud storage.
- You can work with your IT Support Provider to ensure your devices and applications are secured appropriately
- You can view Yale’s Minimum Security Standards.
2. Ensure all applications and software have a Business Associates Agreement (BAA) in place in addition to meeting the MSS.
3. Understand Yale’s Data Loss Prevention (DLP) Program.
- Devices in Yale’s HIPAA Covered entity run our Data Loss Prevention (DLP) program. This program is designed to reduce the risk of unintended exposure to Yale’s sensitive data.
- If you receive a DLP message, you took an action that can put Yale’s high-risk data at risk. The DLP message will look like this:
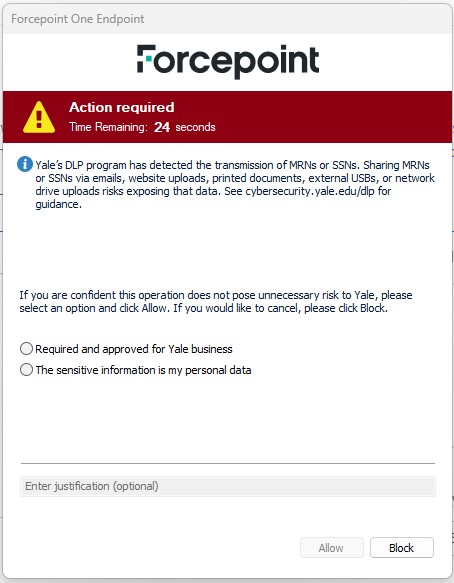
- If you see this message, take it seriously. Make sure you are sending the right information to the right recipient(s). For more information, visit our DLP webpage.
Report Suspicious Cyber Activity Right Away
- If HIPAA data or a device that accessed or stored HIPAA data has been lost or stolen, contact the Information Security Office (ISO) immediately. Call the Information Security Office 24x7 at 203-627-4665.
- It is better to be safe than sorry. Don’t hesitate to report suspicious cyber activity because you are embarrassed or unsure. Go with your gut if something seems unusual or suspicious.
- For more details on reporting an incident, see https://cybersecurity.yale.edu/report
Click with Caution to Protect HIPAA Data
There are many ways we communicate electronically at Yale. Primarily, electronic communication is done through email and text message. These methods of communication are efficient, but they do come with privacy and security risks. Use these tips to “Click with Caution” and use email and SMS text messages securely.
Secure email and text messages
- Email containing PHI can be encrypted by typing “[encrypt]” at the start of the subject line. This should be used whenever emailing outside of the Yale University/YNHH network. For more details on this email security feature, see https://cybersecurity.yale.edu/email-encryption.
- Mobile Heartbeat is available to secure PHI that is sent by text message.
Click with Caution to avoid loss of confidential data
- Phishing messages are fake emails inducing individuals to reveal sensitive or personal information. These messages often appear to come from reputable companies and/or people we trust. They can be very convincing.
- Users need to be vigilant in looking out for phishing attempts, especially those that request a username and password. These scams can also take form in phone calls and text messages.
Steps you can take
- Do not click on links from unexpected or suspicious messages. This is true for email and SMS text messages, even if they appear to come from someone you know or address you directly.
- When you receive an unexpected message, don’t act right away. Go straight to the source by finding alternative ways to contact the person, office, or service directly.
- Be safe, not sorry. The Yale ITS Help Desk will never contact you via SMS text message. Report suspicious messages immediately by calling the Help Desk at 203-432-9000.
- Users need to be careful when approving authentication via Duo or any other two-factor authentication app. Only approve Duo requests when you know you are attempting to login to with your Yale NetID and password.
- Only approve MFA requests when you are actively logging in through Yale’s Central Authentication Service (CAS).
- For more information on how to spot and report these scams, visit the Click with Caution webpage.
If you suspect your NetID account has been compromised, call the Yale Information Security Office 24x7 number: 203-627-4665.